SecOS: 1 Walkthrough
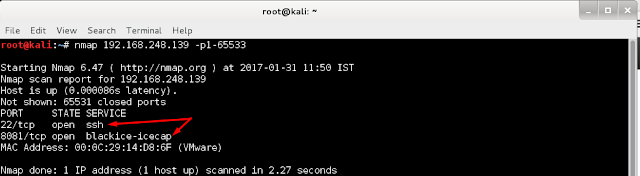
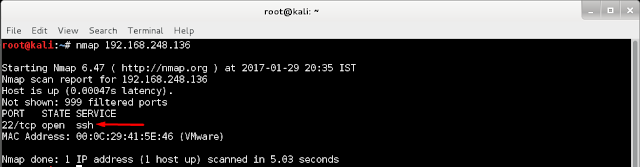
Hi guys i found another awesome CTF on vulnhub so let's walkthrough the Secos . Nmap : Result of nmap shows two ports are open. Let's try to access port 8081. Looks cool ! let's explore website but before open burpsuite and spider this host so that burp can capture some directories. So burp caught a page called hint. Let's visit this page. As always it shows nothing at the front so let's check source code We got three hints, after looking at third hint i quickly goto signup option and created a account and logged in with the same account. Digging around i noticed three important points . Administrator: Spiderman Change password option: Message option: Now we can understand hints simply saying that : We have you conduct a CSRF attack against the administrator i.e spiderman Let's create a form for CSRF attack and the form should auto-submit so as soon as spiderman visits the page his passw