How I bypassed 2-Factor Authentication in a bug bounty program
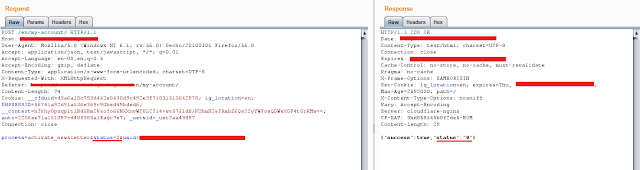
Hello readers, This post is about one of my recent finding in a private bug bounty program on hackerone. For the sake of privacy, let’s call the site as bountyplease.com According to Bountyplease.com scope, they are more interested in Authentication related issues. So I decided to test their 2-Factor Authentication mechanism. As normal 2-Factor Authentication flow the process works in the following steps. 1. User login to account by providing valid email and password 2. A valid OTP send to users register number 3. User fill OTP 4. Login successful But in case if any user lose their phone or SIM card the process works in the following steps. 1. User login to account by providing valid email and password 2. User select other options 3. User provide backup codes 4. Login successful In both above described cases there is also a code flow as following. 1. User login to account by providing valid email and password 2. At this stage bountyplease.com display a pa

Comments
Post a Comment